4. Verifying the VPN Tunnel
(Optional) How to verify that your AWS-Orka VPN tunnel works as expected: check security associations, tunnel status and traffic between Orka and AWS.
Quick navigation
You are here in the workflow: AWS-Orka Connections | 1. AWS Side of the VPN Tunnel | 2. VPN Tunnel Configuration File | 3. Orka Side of the VPN Tunnel | 4. Verifying the VPN Tunnel | VPN Tunnel Troubleshooting
On this page, jump to: Verify that there is an ISAKMP security association between the peers | Verify that there is an IPsec security association between peers | Verify that the tunnel is up | Test traffic and visibility through the tunnel
You need:
- Active VPN connection to your Orka cluster.
- Your Cisco ASAv connection information from the IP Plan.
This part of the workflow is optional.
Verify that there is an ISAKMP security association between the peers
- Run Cisco ASDM-IDM and log in to your firewall.
- In the Cisco ASDM-IDM application toolbar, select Tools > Command Line Interface....
- Select Single Line, enter the following command, and click Send.
show crypto isakmp sa
If the site-to-site VPN connection is configured properly, you should see information about an active IKEv1. For example:
Result of the command: "show crypto isakmp sa"
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: ...
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAs
Verify that there is an IPsec security association between peers
- Run Cisco ASDM-IDM and log in to your firewall.
- In the Cisco ASDM-IDM application toolbar, select Tools > Command Line Interface....
- Select Single Line, enter the following command, and click Send.
show crypto ipsec sa
If the site-to-site VPN connection is configured properly, you should see a detailed log. For example:
Result of the command: "show crypto ipsec sa"
interface: Outside
Crypto map tag: amzn_vpn_map_1, seq num: 1, local addr: ...
access-list acl-amzn extended permit ip any ...
local ident (addr/mask/prot/port): ...
remote ident (addr/mask/prot/port): ...
current_peer: ...
....
inbound esp sas:
...
outbound esp sas:
...
Verify that the tunnel is up
Currently, Amazon lets you create a site-to-site VPN where at all times one tunnel is active (up) and one is passive (down). A monitoring service checks frequently if the active tunnel is up and, if not, brings the passive tunnel up instead. This ensures minimal downtime.
- Log in to your AWS Management Console and access your VPC service. In the top right corner of the screen, make sure that you're working in the correct region.
- In the sidebar, locate the Virtual Private Network menu and select Site-to-Site VPN Connections.
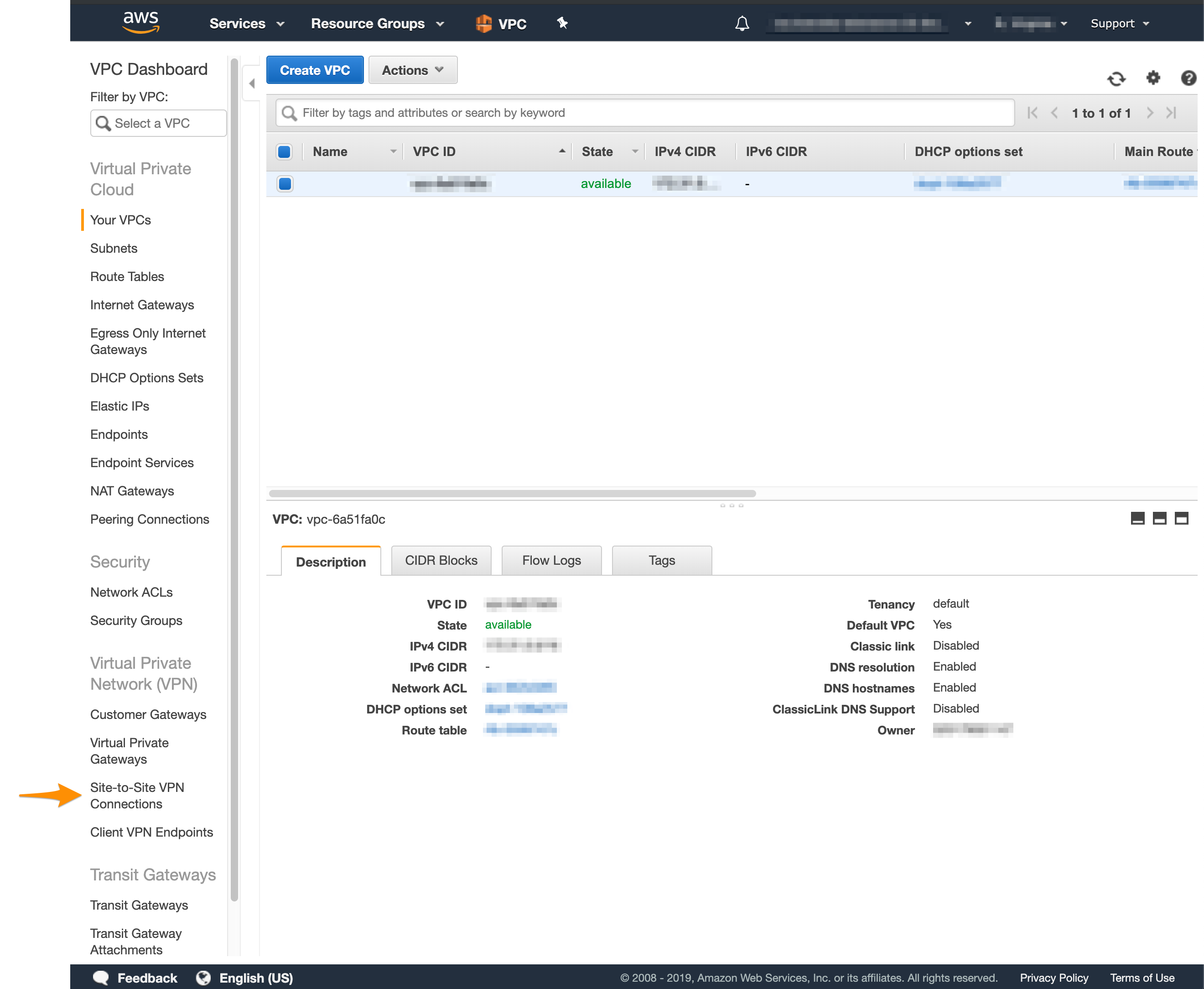
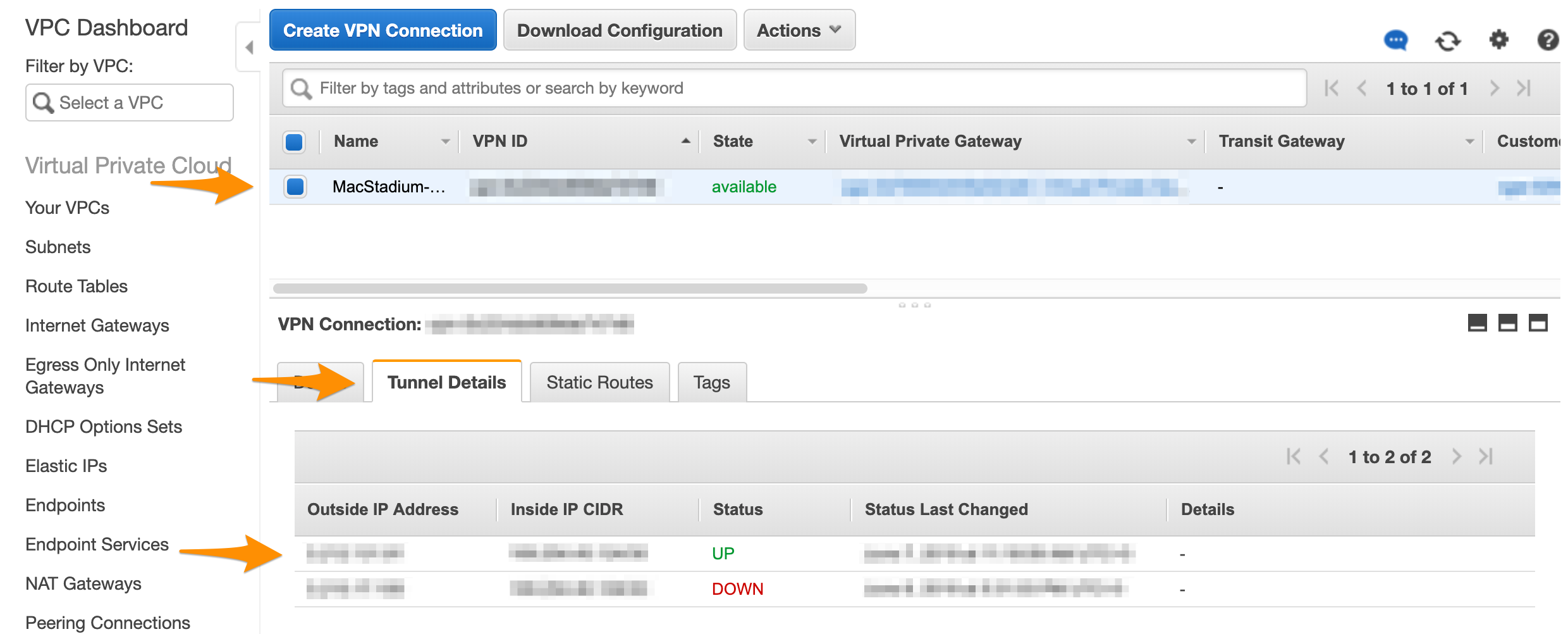
- Select your VPN from the list and inspect the details at the bottom of the screen.
- Click Tunnel Details and verify that one of the tunnels is up.
Test traffic and visibility through the tunnel
Amazon VPC Documentation: How to Test the Customer Gateway Configuration
What's next
Updated over 5 years ago
